Which of the Following Best Describes a Distributed Denial-of-service Attack
Lost sales corporate liability eg Sarbanes-Oxley. This group of writers have passed strict English tests plus tests from their fields of specialization.
What Is A Ddos Attack Identifying Denial Of Service Attacks
The DoS attacks that most people have heard about are those launched against high profile websites since these are frequently reported by the media.
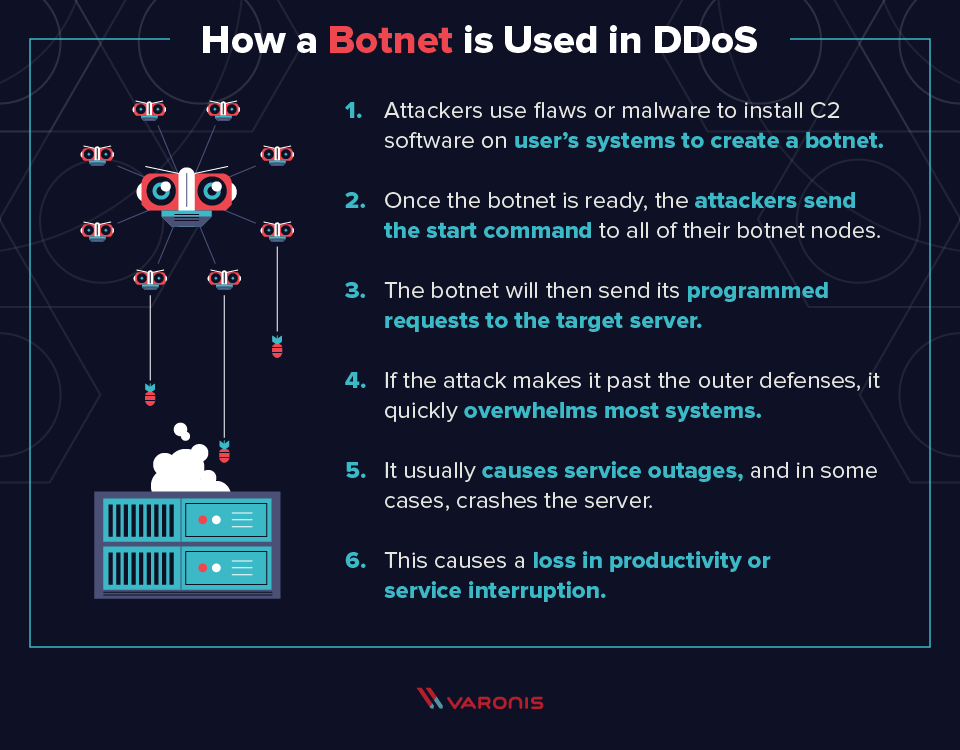
. However attacks on any type of system including industrial control systems which. The phrase cyber attack commonly describes a politically motivated attack whether by states or non-state actors like terrorists. Denial of service or DoS describes the ultimate goal of a class of cyber attacks designed to render a service inaccessible.
It began in the early hours of Feb. This writers are also assigned a. Best available This refers to a group of writers who are good at academic writing have great writing skills but are new in our team of writers.
A destructive attack followed in which a malicious software command sent across the network rendered tens of thousands of modems across Europe inoperable by overwriting key data in their internal memory Viasat said. 15 they hit the defense ministry and two banks with a distributed denial of service or DDOS attack that brought their websites down. Often cyber attacks use information and communication technologies ICTs to.
This means they are able to deliver high quality assignments. This means they recently joined the team. 24 with a distributed denial-of-service onslaught that knocked a large number of modems offline.
Some are expressed in terms of revenue. Impacts are consequences that the business must face if there is a successful attack. Cyber crime most often describes activity for purely criminal ends although this definition is shifting as cyber crime grows in sophistication and magnitude.
Also important are impacts to the companys marketing abilities. An attack occurs when an attacker acts and takes advantage of a vulnerability to threaten an asset.

0 Response to "Which of the Following Best Describes a Distributed Denial-of-service Attack"
Post a Comment